Create Certificates
Open up the Certificates window by going to /System -> Certificates. Hit the + to add a new certificate
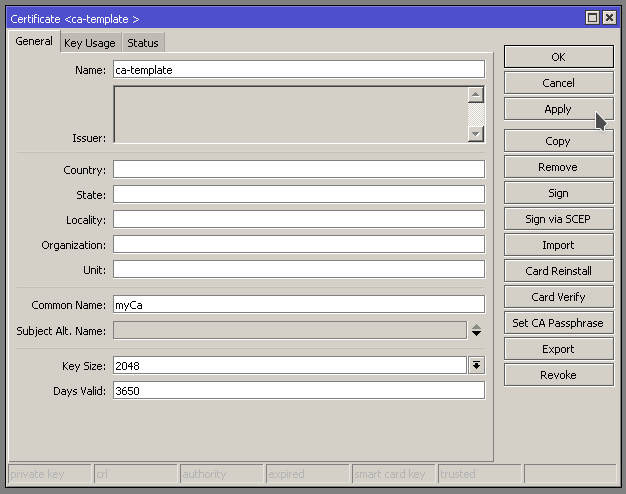
Create Certificate Authority Certificate
First we are going to create a Certificate Authority template
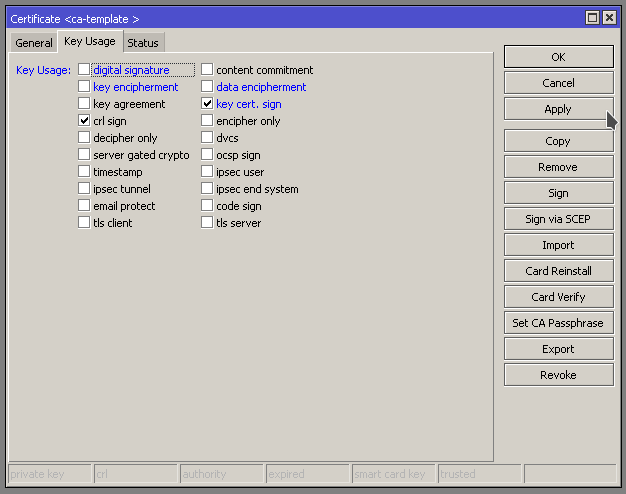
Specify the key usage to “crl sign” and “key cert. sign” and apply
Setup Server Certificate
Now we are going to create a server template
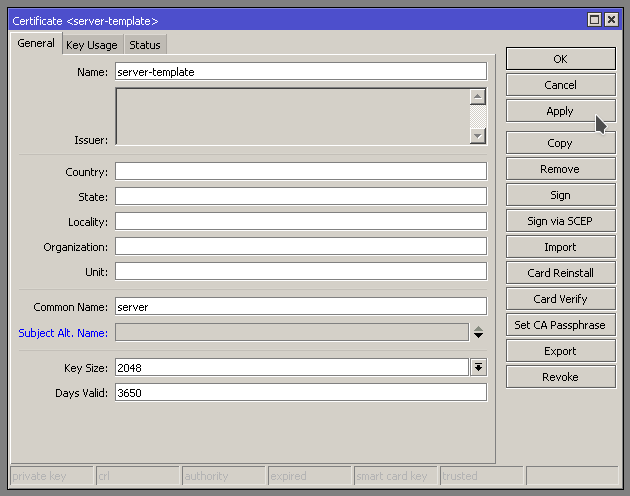
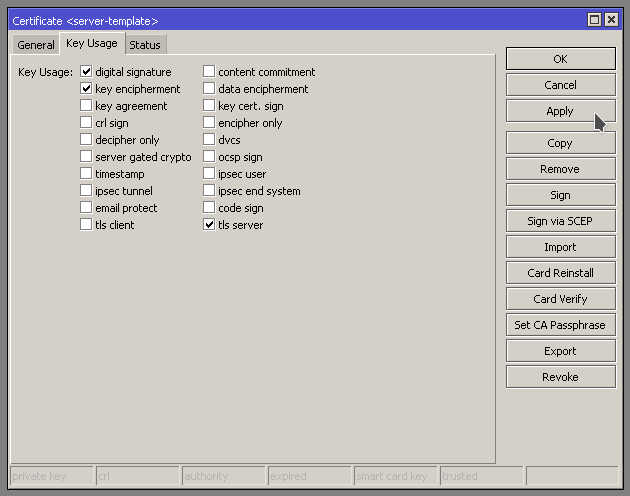
We need to specify “Digital signature, key encipherment, and tls server” You may need to enable/disable more depending on your use case scenario. In this case we are setting it up for OpenVPN.
Sign Templates
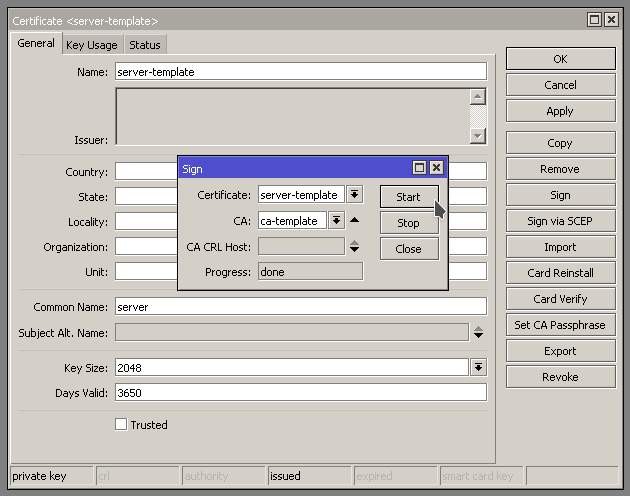
First we need to sign the ca-template by opening up the the Certificate and hitting Sign on the right hand side. Should get the little Sign window pop up.
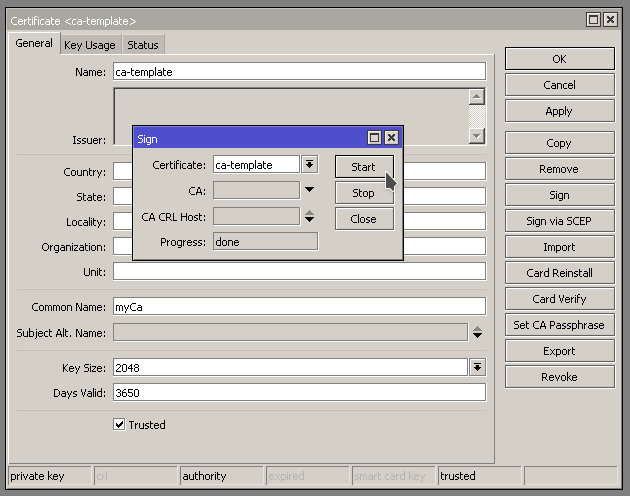
Progress will show done when it is finished signing.
Next we need to sign the server-template. When Signing the server template, specify the ca-template in the CA: field. See below