You thought everything went well with your NixOS install, you reboot, enter your username and password, and bam! Login incorrect.
Okay, try it again.
Login incorrect
Hmm…
Let’s try root. Nope, same thing…
If you don’t enter the password in correctly for root at the end of an installation, there will not be a root password, hence you can not log in.
Best way to keep this from happening is to make sure the password is set up before rebooting.
If you are one of those unfortunate souls who entered the wrong root password and missed the warning at the end of the installation
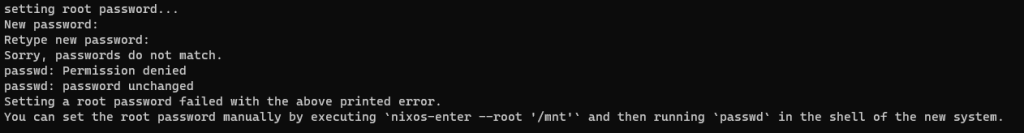
Try the following.
nixos-enter --root '/mnt'
Note: If you already rebooted, boot up on the minimum USB drive, mount the root partition, then run the nixos-enter command.
mount /dev/disk/by-label/nixos /mnt nixos-enter --root '/mnt'
passwd to set the root password. You can also set your user password with
passwd username
Change username to your username.
Reboot and login!