Install hashcat
apt install hashcat
Find LUKS Volume
bob@localhost:~/$ dmesg ... [ 1057.776074] sd 0:0:0:0: [sda] Write Protect is off [ 1057.776074] sd 0:0:0:0: [sda] Mode Sense: 43 00 00 00 [ 1057.776593] sd 0:0:0:0: [sda] Write cache: enabled, read cache: enabled, doesn't support DPO or FUA [ 1057.780234] sda: sda1 [ 1057.783346] sd 0:0:0:0: [sda] Attached SCSI removable disk bob@localhost:~/$
From the above we see that the drive we just pluGged into the system is “sda” so our path and partition is “/dev/sda1”
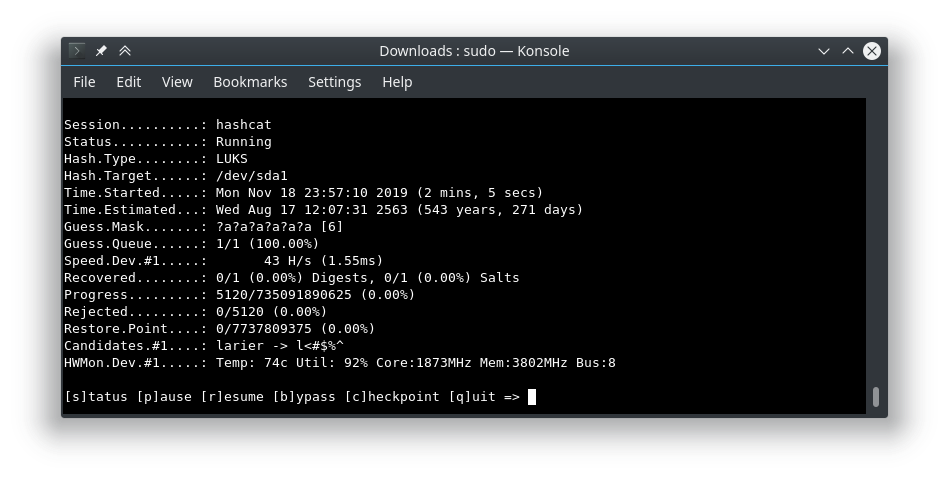
Run hashcat
The following command will run hashcat against “/dev/sda1”, change if the encrypted partition is different. Mode is to brute force every 8 numeric character combination. Refer to the following link to learn more about mask attacks.
https://hashcat.net/wiki/doku.php?id=mask_attack
Note: You should be able to dump the header and work off of that as well.
sudo hashcat -a 3 -m 14600 /dev/sda1 ?d?d?d?d?d?d?d?d