In this post we are going to setup Exim to add “[External]” to the email subject if it originates from outside of the local domain.
Thanks to Sam for this post. It was extremely helpful.
https://tech.saqr.org/2020/01/for-incoming-email-not-from-our-domain.html
Steps
- Create a new Exim Filter
- Enable Filter
Create an Exim Filter
SSH to the server and create a Exim filter. In cPanel there are in /usr/local/cpanel/etc/exim/sysfilter/options/. You can name the filter what ever you want.
vi /usr/local/cpanel/etc/exim/sysfilter/options/external_email_warningChange “incredigeek.com” to your domain name.
You can also change “[External]” to whatever you want to be prepended to the subject.
if
$header_to: contains "@incredigeek.com>"
and $header_from: does not contain "@incredigeek.com>"
and $header_subject: does not contain "[External]"
then
headers add "Old-Subject: $h_subject:"
headers remove "Subject"
headers add "Subject: [External] $h_old-subject"
headers remove "Old-Subject"
endifSave the file.
Enable Custom Exim Filter
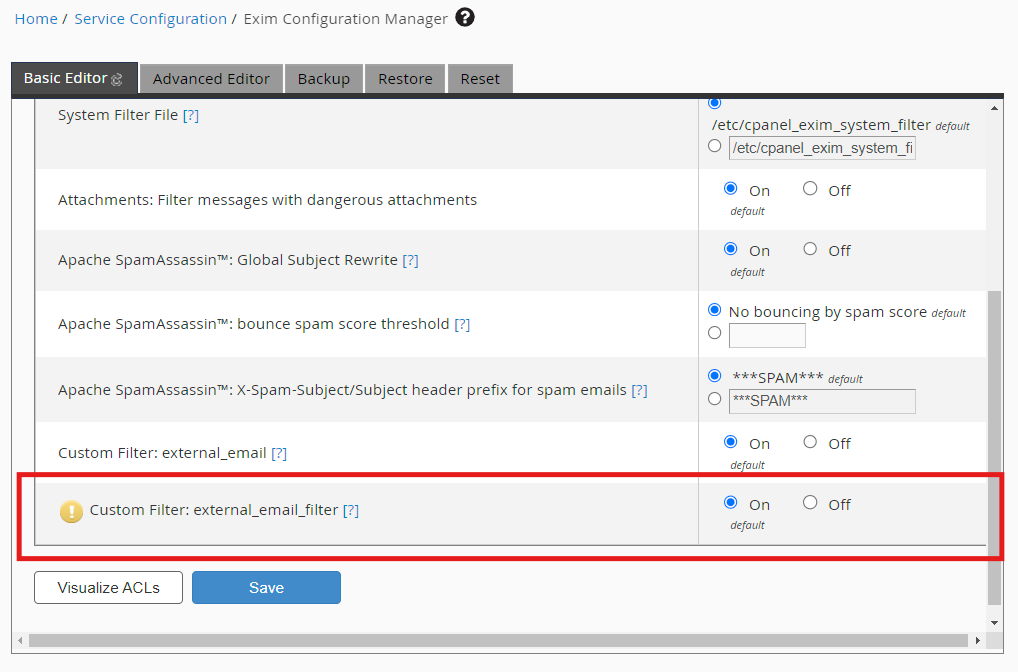
Now log into WHM, go to Service Configuration > Exim Configuration Manager > Basic Editor > Filters
At the bottom of the filters, you should see a new “Custom Filter: external_email_filter”
This is the filter you just created. Make sure it is On, and Save changes.
There you go! Any email you receive now that is from an external domain should now have “[External]”, or whatever you specified, prepended to the subject.
If you run into any errors, try reviewing the panic log to see if there are any syntax errors.
Troubleshooting
You can use tail to follow the panic log to verify you have all the syntax correct.
tail /var/log/exim_paniclog -f