Unfortunately, encrypting a file on Windows with a simple password is not super simple. While Windows does now support other compression formats (RAR, 7-Zip) it does not support encryption for them.
Currently, Windows natively supports the ZipCrypto algorithm. No AES. Note that the ZipCrypto algorithm is not considered secure, and shouldn’t be used for highly confidential data.
The following method, you will need 7-Zip to create the archive, but you won’t need it for decryption as Windows has built in support for ZipCrypto decryption.
To create the archive, you will need 7-Zip installed. Right click on your file/folder -> 7-Zip -> Add to Archive.
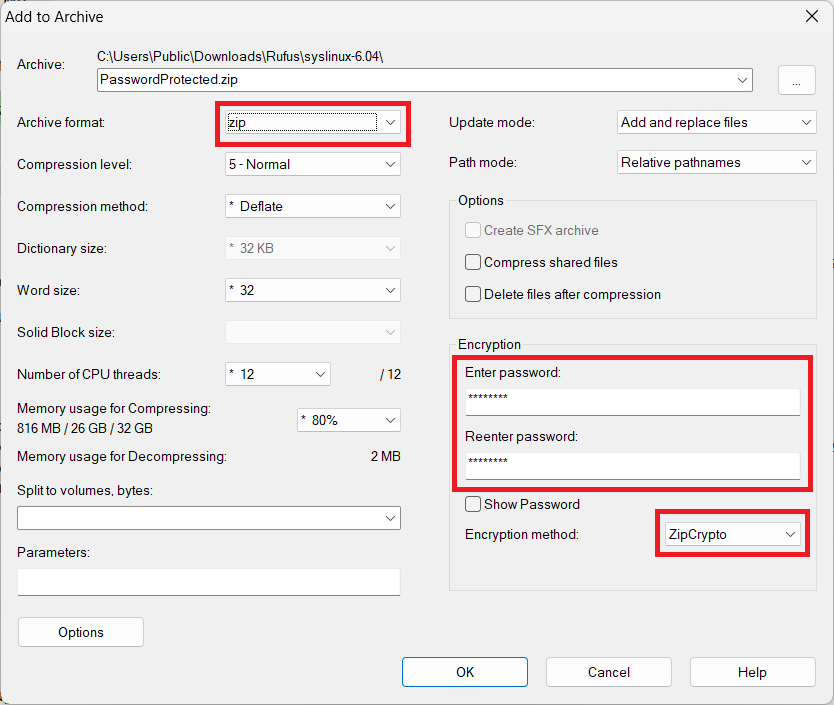
You should be presented with a similar window.
Change Archive format to zip
Enter the password
Ensure that the Encryption method is ZipCrypto
Hit OK to create the Archive.
You can now transfer the password protected archive to a new machine. You’ll be prompted for the password when you extract the archive.