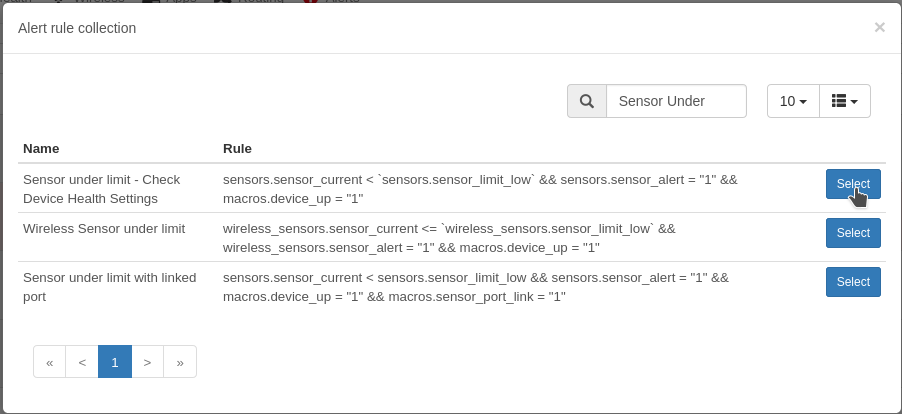
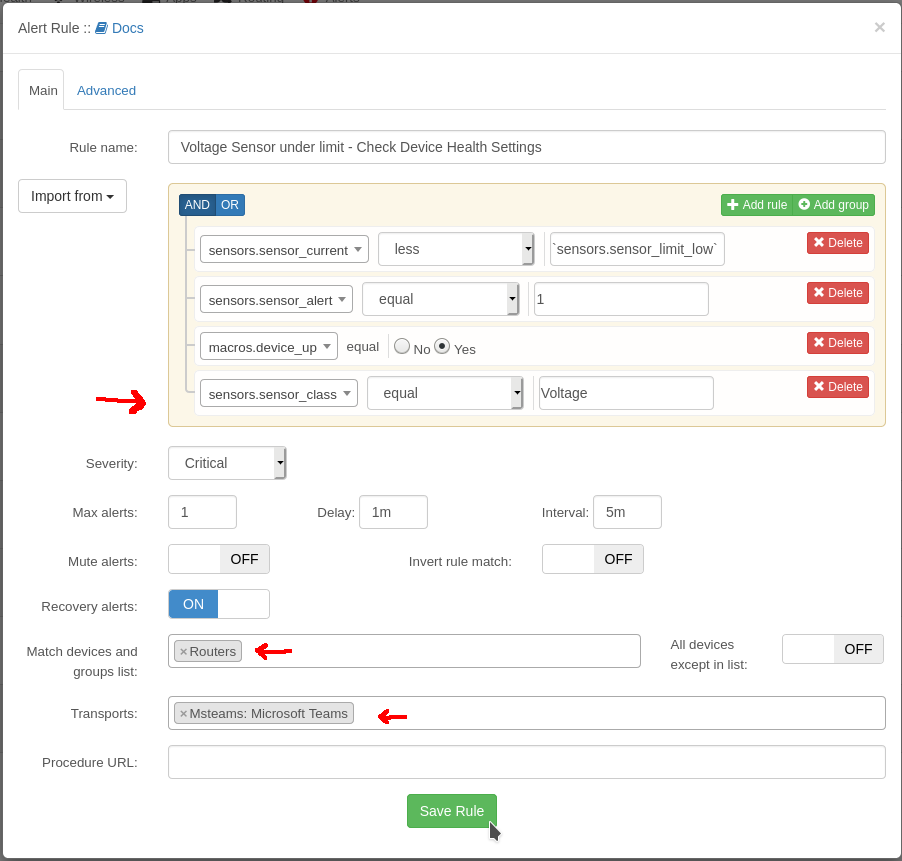
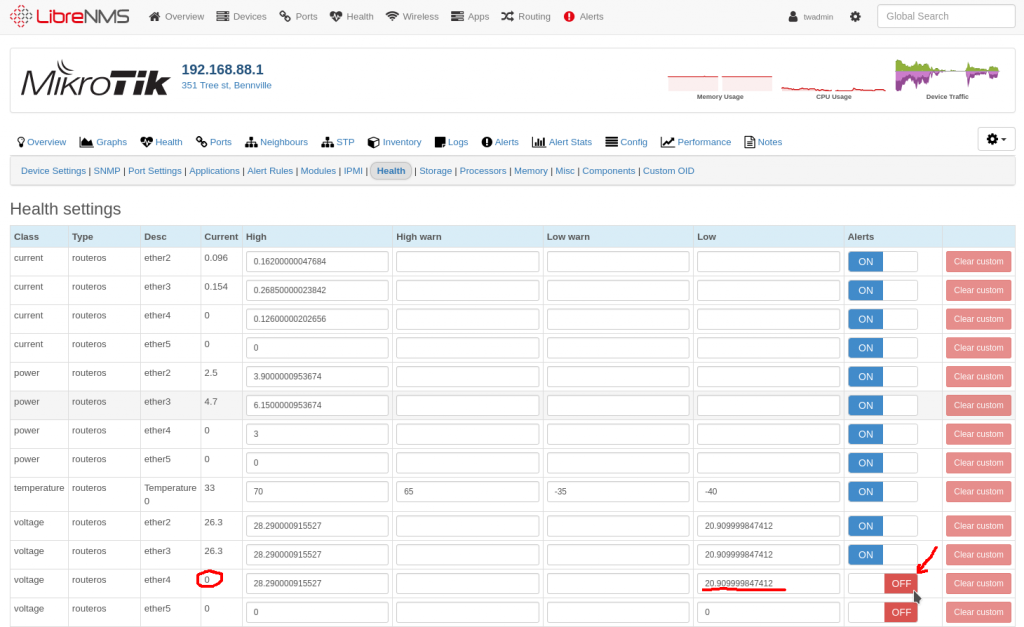
In the cambium cloud you can retrieve a config from a router, modify it and reapply it or make a template from it. All the passwords are “encrypted” so you can’t read what the WiFi password is for example.
Example config line looks like
WPAPSK1=[c760ba8ffe65c669]
Looks like it uses some sort of des3 hex encryption.
Fortunately there is a utility on the routers we can use to decrypt the encrypted string.
First we need a router that we can SSH into.
Info on the encryption
The Cambium router uses the 3des_hex utility to decrypt and encrypt strings
It is located /sbin/3des_hex
Decrypting a password
Decrypting is super easy.
3des_hex -d "c760ba8ffe65c669"
Replace the key with the key you want to decrypt.
Encrypting a password
Not really sure if this would ever be needed, but you can use the -e option to encrypt a string
3des_hex -e "12345678"
More info.
It looks like it needs the lib file “/lib/libuClibc-0.9.33.2.so”
/sbin/3des_hex is where the main file is stored though.
The config_manager.sh script in /sbin has the functions that encrypt and decrypt the config lines.
TMP_FILE="/tmp/tmp_cfg"
TMP_FILE2="/tmp/tmp_cfg2"
TMP_FILE_DECRYPT="/tmp/tmp_cfg_decrypt"
TMP_MFK_FILE="/tmp/multi_function_key.cfg"
decrypt_key="asdfghjkl";
SNMP_DECRYPT_FILE="/etc/cambium/cambium_default.decrypt"
DotFactoryFile="/etc_ro/DoNotFactory.name"
# when security encrypt enable , decrypt.
handle_file_dec()
{
local enc_enable=`dev_manage_stat_get has_config_enc`
if [ "$enc_enable" != "1" ]; then
return 0
fi
SecParamListFile="/etc_ro/ConfigFileSecParam"
[ -x "/sbin/3des_hex" ] || return 0
[ -f $SecParamListFile ] || return 0
[ -z "$1" ] && return 1
awk -F '=' 'ARGIND==1{pname[$0]}ARGIND>1&&($1 in pname){print $0}' $SecParamListFile $1 > $1.tmp
awk '{if($0~/.+\=\[.*\]/){sub("\=","\|");print $0;}else{print $0}}' $1.tmp > $1.tmp1
rm -f $1.tmp
awk -F'|' '{if($2~/\[.*\]/){len=length($2);value=substr($2,2,len-2);while(("3des_hex -d \""value"\""|getline line)>0){printf("%s=%s\n",$1,line);}close("3des_hex -d \""value"\"");}else{print $0}}' $1.tmp1 > $1.tmp2
rm -f $1.tmp1
echo "" >> $1
cat $1.tmp2 >> $1
rm -f $1.tmp2
}