By default the U Installer redirects you to a page asking you to download the app. You can get to the actual U Installer web page by going to https://169.254.169.169
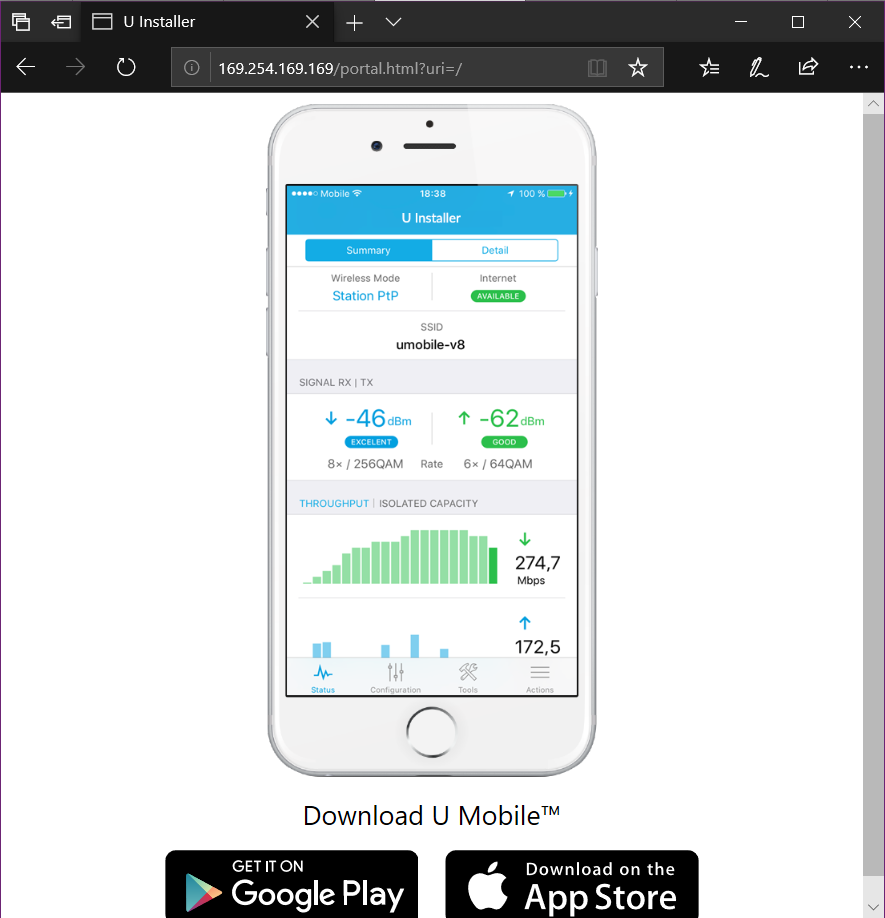
It has the same interface as a regular Airmax M equipment.


By default the U Installer redirects you to a page asking you to download the app. You can get to the actual U Installer web page by going to https://169.254.169.169


It has the same interface as a regular Airmax M equipment.

SSH
Looks like Default SSH port is 27149
Software
Runs Quagga
CELL> show version Quagga 0.99.21 (). Copyright 1996-2005 Kunihiro Ishiguro, et al.
Settings
show network config
CELL> enable CELL# show network % Command incomplete. CELL# show network config network.loopback=interface network.loopback.ifname='lo' network.loopback.proto='static' network.loopback.ipaddr='127.0.0.1' network.loopback.netmask='255.0.0.0' network.lan=interface network.lan.proto='static' network.lan.ipaddr='192.168.150.1' network.lan.netmask='255.255.255.0' network.lan.mtu='1496' network.lan.ifname='eth2.3' network.wan=interface network.wan.ifname='eth2' network.wan.media='copper' network.wan.proto='dhcp' network.defRouteIf=defRouteIf network.defRouteIf.defRouteIf='wan' CELL#
Users
CELL# show user User Permission State --------------------------------- admin admin unlocked anonymous admin unlocked --------------------------------- CELL#
User commands
CELL# user USERNAME User name add Add user delete Delete user lock User lock role User role unlock User unlock CELL# user
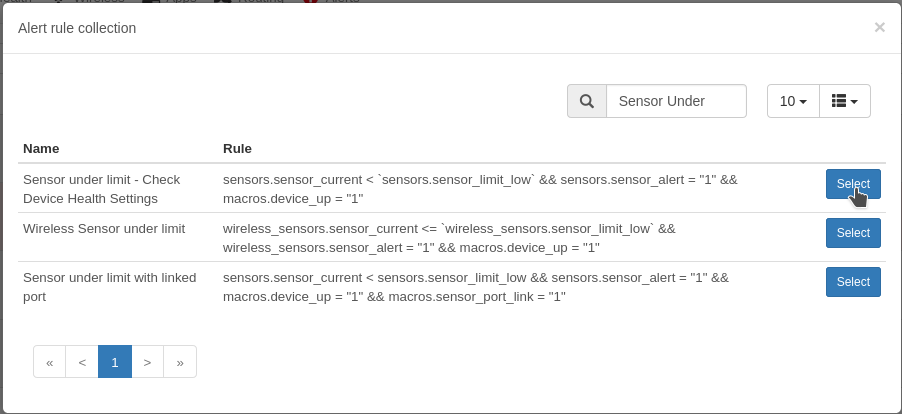
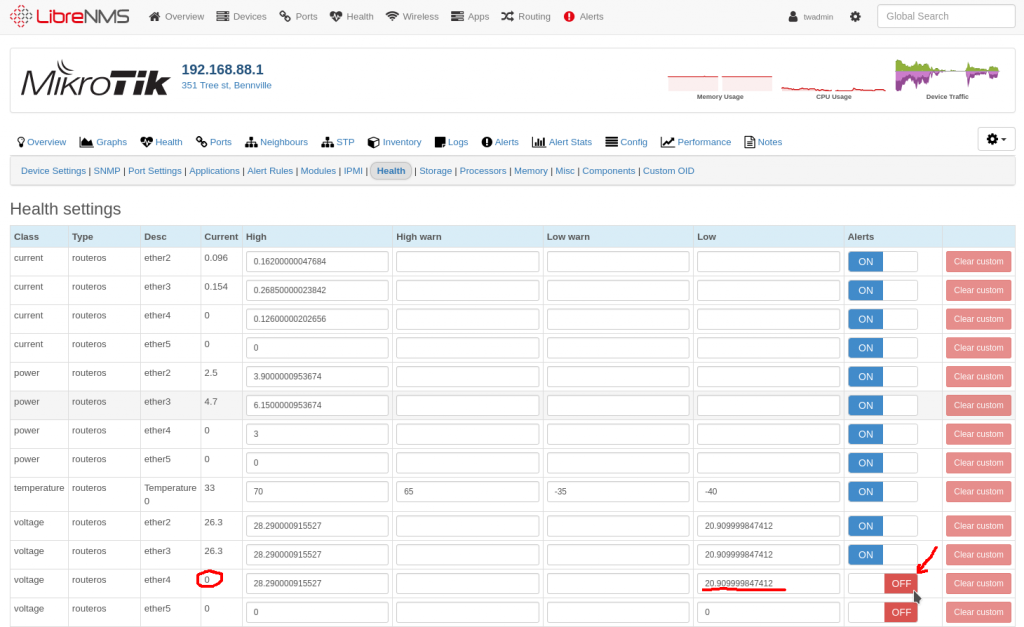
Go to “Alerts -> Alert Rules” Then “Create rule from Collection”
Search for “Sensor under limit” and Select
Add another rule to limit to just the Voltage Sensors by using the “sensors.sensor_class = Voltage”
Select your Groups and Transports and Save.
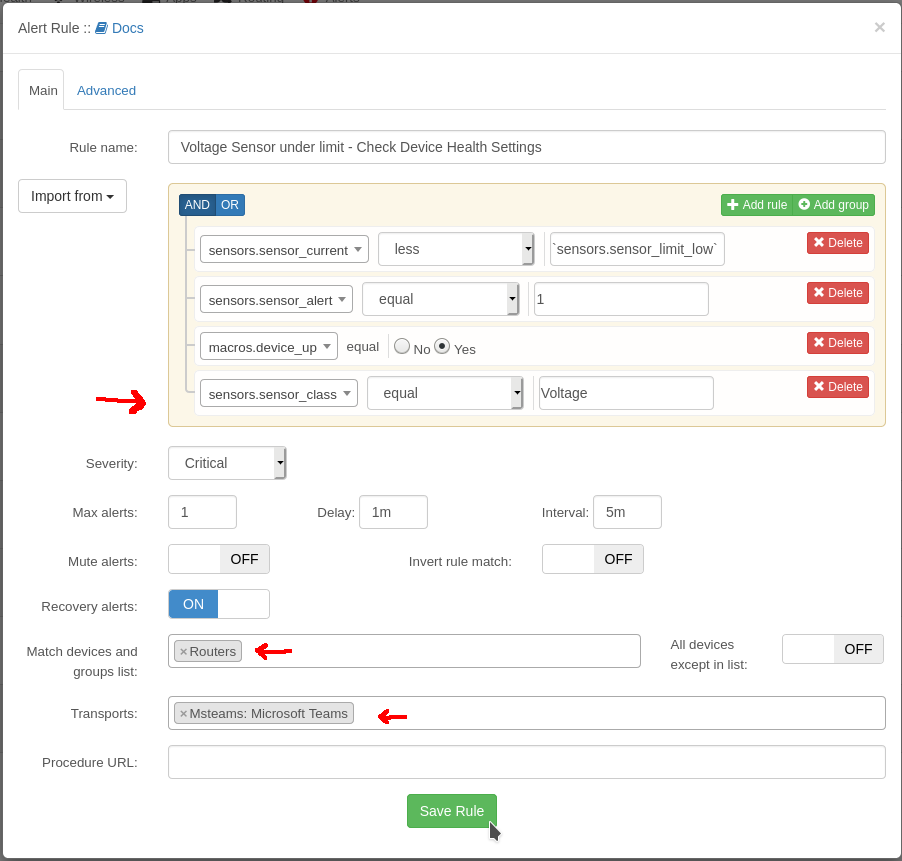
You may get some alerts because there are some ports that do not have any any voltage on them. You can disable them on a per device basis by going to the “device -> Edit -> Health” and turning alerts off
Problem – Need 2.4 Ghz network enabled and SSID set to WiFi. Wireless router is behind a NAT, using UNMS to ssh into the radio, and from the radio ssh into hAP. Enter/Return key not working to run commands, so running the commands over ssh from the radio.
WA.v8.4.2# ssh admin@192.168.88.2 'interface wireless print'
admin@192.168.88.2's password:
Flags: X - disabled, R - running
0 name="wlan1" mtu=1500 l2mtu=1600 mac-address=74:4D:28:0F:69:B3
arp=enabled interface-type=Atheros AR9300 mode=station ssid="MikroTik"
frequency=2412 band=2ghz-b/g channel-width=20mhz secondary-channel=""
scan-list=default wireless-protocol=any vlan-mode=no-tag vlan-id=1
wds-mode=disabled wds-default-bridge=none wds-ignore-ssid=no
bridge-mode=enabled default-authentication=yes default-forwarding=yes
default-ap-tx-limit=0 default-client-tx-limit=0 hide-ssid=no
security-profile=default compression=no
1 R name="wlan2" mtu=1500 l2mtu=1600 mac-address=74:4D:28:0F:69:B2
arp=enabled interface-type=Atheros AR9888 mode=ap-bridge ssid="WiFi"
frequency=5180 band=5ghz-n/ac channel-width=20mhz secondary-channel=""
scan-list=default wireless-protocol=802.11 vlan-mode=no-tag vlan-id=1
wds-mode=disabled wds-default-bridge=none wds-ignore-ssid=no
bridge-mode=enabled default-authentication=yes default-forwarding=yes
default-ap-tx-limit=0 default-client-tx-limit=0 hide-ssid=no
security-profile=default compression=no
WA.v8.4.2# ssh admin@192.168.88.2 'interface wireless set disabled=no ssid=WiFi wlan1'
admin@192.168.88.2's password:
WA.v8.4.2# ssh admin@192.168.88.2 'interface wireless print'
admin@192.168.88.2's password:
Flags: X - disabled, R - running
0 name="wlan1" mtu=1500 l2mtu=1600 mac-address=74:4D:28:0F:69:B3
arp=enabled interface-type=Atheros AR9300 mode=station ssid="WiFi"
frequency=2412 band=2ghz-b/g channel-width=20mhz secondary-channel=""
scan-list=default wireless-protocol=any vlan-mode=no-tag vlan-id=1
wds-mode=disabled wds-default-bridge=none wds-ignore-ssid=no
bridge-mode=enabled default-authentication=yes default-forwarding=yes
default-ap-tx-limit=0 default-client-tx-limit=0 hide-ssid=no
security-profile=default compression=no
1 R name="wlan2" mtu=1500 l2mtu=1600 mac-address=74:4D:28:0F:69:B2
arp=enabled interface-type=Atheros AR9888 mode=ap-bridge ssid="WiFi"
frequency=5180 band=5ghz-n/ac channel-width=20mhz secondary-channel=""
scan-list=default wireless-protocol=802.11 vlan-mode=no-tag vlan-id=1
wds-mode=disabled wds-default-bridge=none wds-ignore-ssid=no
bridge-mode=enabled default-authentication=yes default-forwarding=yes
default-ap-tx-limit=0 default-client-tx-limit=0 hide-ssid=no
security-profile=default compression=no
WA.v8.4.2# ssh admin@192.168.88.2 'interface wireless registration-table print'
admin@192.168.88.2's password:
# INTERFACE RADIO-NAME MAC-ADDRESS AP SIGNAL... TX-RATE
0 wlan2 A7:32:54:EE:E4:35 no -77dBm... 18Mbps
1 wlan2 34:7A:F4:43:AD:81 no -69dBm... 6Mbps
WA.v8.4.2# exit