What we are going to do is create a proxy using ssh so we can tunnel our web traffic in Firefox through it.
First, launch putty and setup a SSH connection like you normally would.
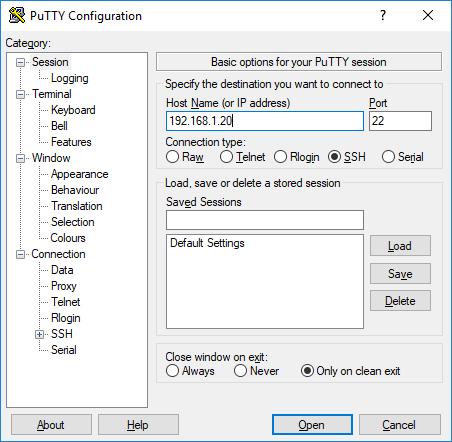
Next, in Putty, go to the Connection, SSH, Tunnels. Set source port, change to Dynamic, and add. In this example we are using port 1880.
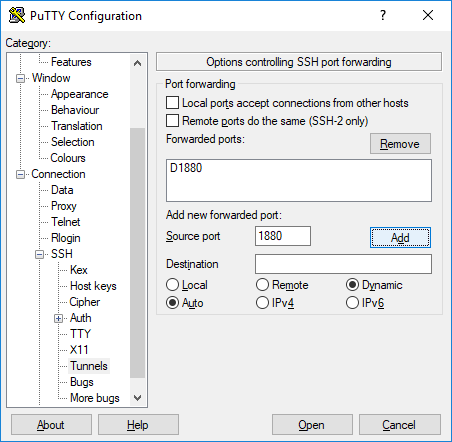
After you have it set, Open the connection and log in.
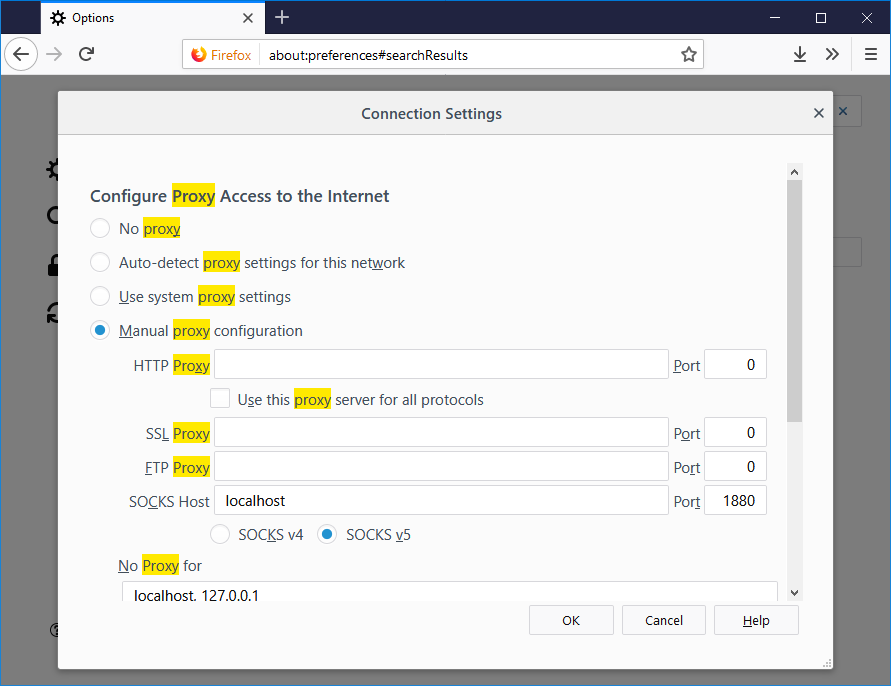
Now go to the Proxy settings in Firefox. You can open new tab, type about:preferences, hit enter, search proxy.
Set to Manual proxy configuration, then under SOCKS Host put localhost and the port number from Putty above, 1880 in our case.
 You should now be running over the proxy, can test by running a whats my ip address.
You should now be running over the proxy, can test by running a whats my ip address.
This can be particularly useful in cases where you need to access a local IP address range on something like a Ubiquiti radio or router. Or you need to check something from a different IP address.



