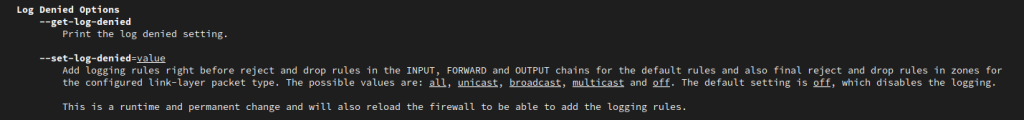
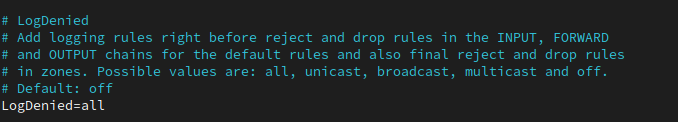
The following is a great article explaining the main Exim log.
https://forums.cpanel.net/resources/reading-and-understanding-the-exim-main_log.383/
The following are some helpful tips from the post.
Search log by email address
You can search for specific addresses with the exigrep. Replace email@address with the email address of interest.
exigrep email@address /var/log/exim_mainlog
Message Direction
Looking at entries in the main log, some of the messages will have an indicator from the following table that tell us the status of the message and/or where it came from or went.
| <= | Indicates the arrival of a message to Exim for handling |
| => | Shows a normal message delivery |
| -> | Additional address for the same delivery, i.e. an Email forwarder. |
| >> | cutthrough is a router precondition This option requests delivery be attempted while the item is being received. It is usable in the RCPT ACL and valid only for single-recipient mails forwarded from one SMTP connection to another. If a recipient-verify callout connection is requested in the same ACL it is held open and used for the data, otherwise one is made after the ACL completes. |
| *> | delivery suppressed by -N |
| ** | delivery failed; address bounced |
| == | delivery deferred; temporary problem |
| <> | For “<>” from the exim manual; Additionally, you will often find A bounce message is shown with the sender address “<>”, and if it is locally generated, this is followed by an item of the form R=<message id> |
Some other posts that may be helpful while troubleshooting mail deliveries.