Enabling logging on firewall rules can be beneficial for tracking why a certain rule is not behaving as you intended.
Enabling logging is relatively straight forward.
- Enable Firewall Logging
- Check Logs
- Disable Firewall Logging (Optional)
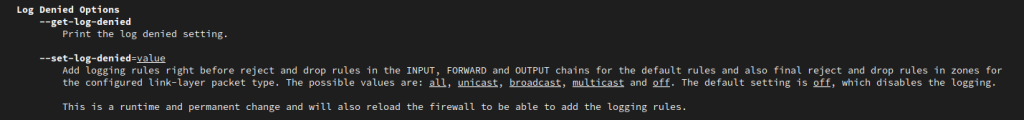
Enable Firewall Logging
Quickest way to enable logging is to run
sudo firewall-cmd --set-log-denied=all
This changes the options in the /etc/firewalld/firewalld.conf config file. Options include all, unicast, broadcast, multicast, and off
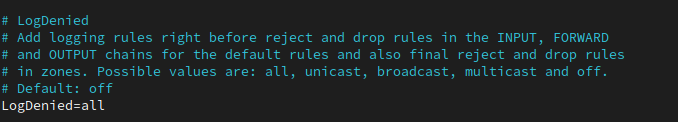
The command also reloads the firewall so manually restarting the firewall is necessary.
Checking Logs
You can use dmesg to view the failed attempts or you can follow the messages log and filter to just show the rejects
sudo tail -f /var/log/messages | grep -i REJECT
You can now try to access the server or run a test to trigger a log event. In my case I tried initiating a SSH connection.
Oct 1 16:32:10 localhost kernel: FINAL_REJECT: IN=eno1 OUT= MAC=f8:ab:98:12:fe:11:a1:ec:a6:00:67:3e:97:00 SRC=192.168.1.1 DST=192.168.88.2 LEN=60 TOS=0x08 PREC=0x40 TTL=59 ID=43080 DF PROTO=TCP SPT=38192 DPT=22 WINDOW=52240 RES=0x00 SYN URGP=0
Interesting bits are bolded. Our destination port it 22 “ssh” and our source address is 192.168.1.1. If I want this IP to access the server, I’ll need to add the 192.168.1.1 IP range in the allowed IP ranges.
Disable Logging (Optional)
After you have finished troubleshooting your problem, you may want to turn the logging feature off so you don’t fill up the logs with failed entries.
You can turn it off with
sudo firewall-cmd --set-log-denied=off
We can verify that logging is off by running
sudo firewall-cmd --get-log-denied
If the firewall logging option is off it will return “off”
The following site has some more information and alternative ways
https://www.cyberciti.biz/faq/enable-firewalld-logging-for-denied-packets-on-linux/
