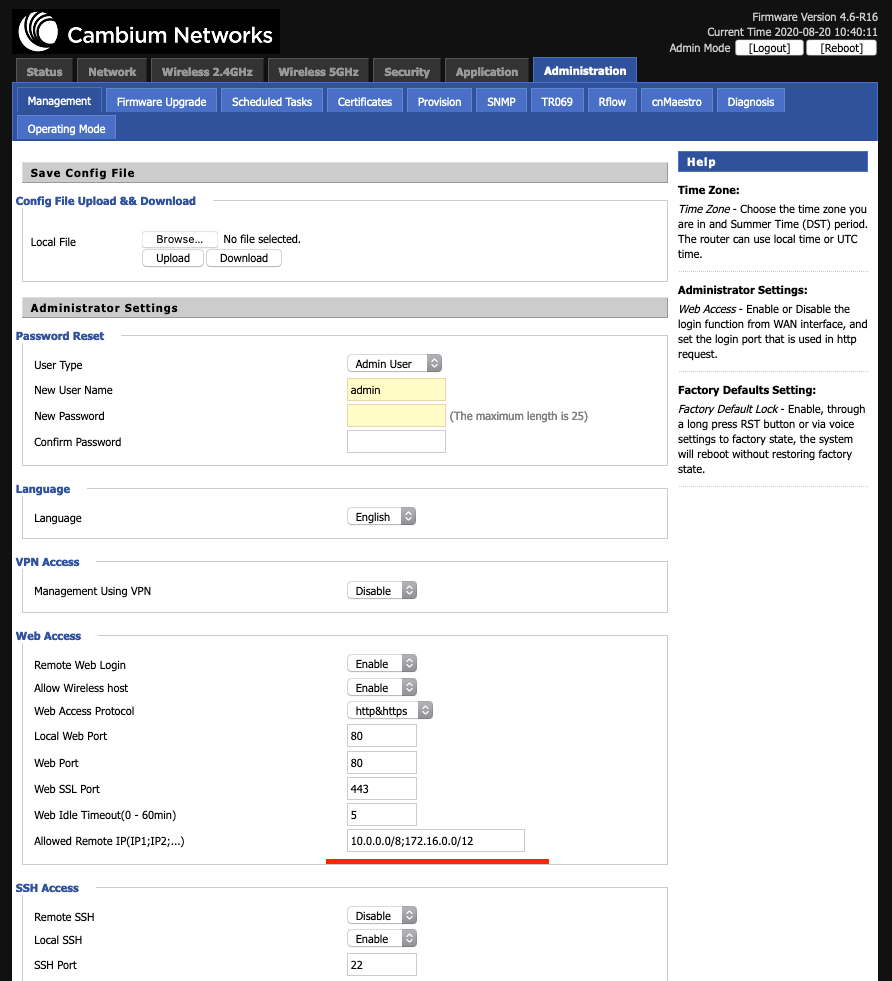
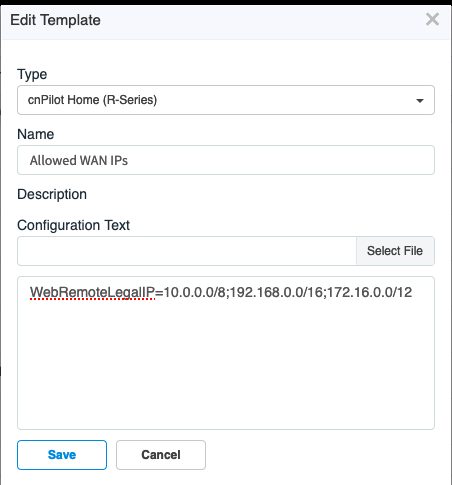
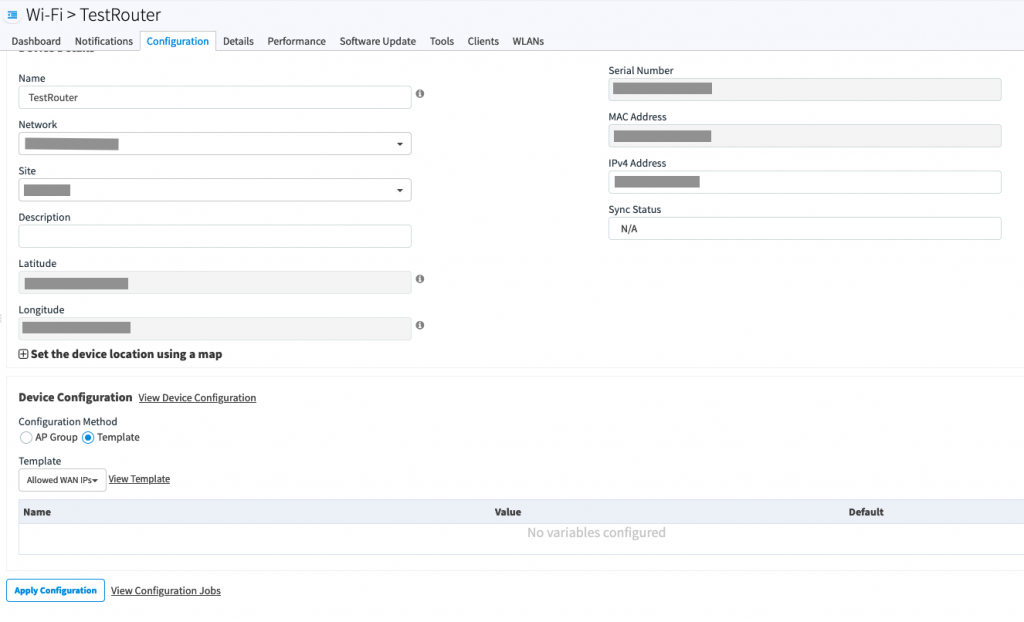
By default the passwords are “encrypted” so you can not tell what the password is.
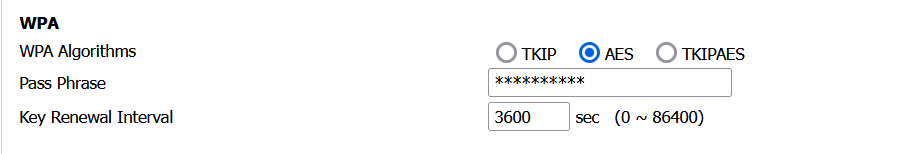
We covered decrypting the passwords from the config file from cambium cloud. But what about a local router that is not connected to the cloud. What then?
Thankfully everything you need is on the router. We’ll need to use the command line tools.
1. Enable SSH
First verify that SSH is enabled.
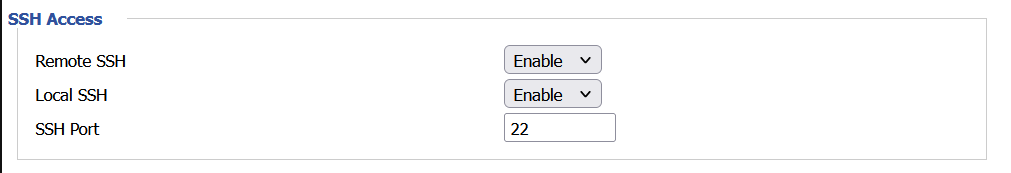
2. SSH into router
You may need to specify the “diffie-hellman-group1” option if it throws an error.
ssh admin@192.168.11.1 -o KexAlgorithms=+diffie-hellman-group1-sha1
3. Extract Encrypted WiFi Password from config
The config file is stored in “etc/cambium/bkup-config.txt”
cat etc/cambium/bkup-config.txt | grep
This should dump the encrypted password(s).
Example Output.
WPAPSK1=[c760ba8ffe65c669] RTDEV_WPAPSK1=[c760ba8ffe65c669]
4. Decrypt WiFi Password
Now we can decrypt the password. Replace the string at the end with the encrypted string
3des_hex -d c760ba8ffe65c669
It should now display the decrypted password
# 3des_hex -d c760ba8ffe65c669 12345678#
Note that it puts the # symbol after the password and if you try to type something in, it clears the line. you can use the following to have cleaner output.
echo $(3des_hex -d c760ba8ffe65c669 )
That will print the password on it’s own line
# echo $(3des_hex -d c760ba8ffe65c669 ) 12345678 #