Manually adding the UniFi Protect self signed certificate can be helpful if you are accessing the controller over the local network. It has the benefit of letting your browser remember the password if wanted and not having to verify the certificate.
First we need to acquire the certificate.
Acquire UniFi Protect Certificate
In a Chrome based web browser, go to the IP address of the UniFi Protect NVR
Click in the URL bar where is says “Not secure” -> Certificate -> Details -> Copy to file
Follow the export Wizard. You can use the default settings.
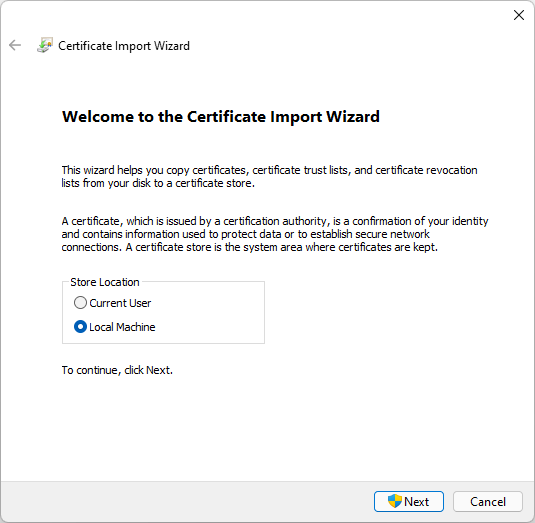
Import Certificate
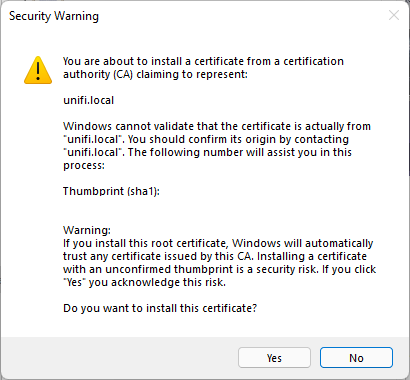
You can now import the certificate by double clicking on the cert.
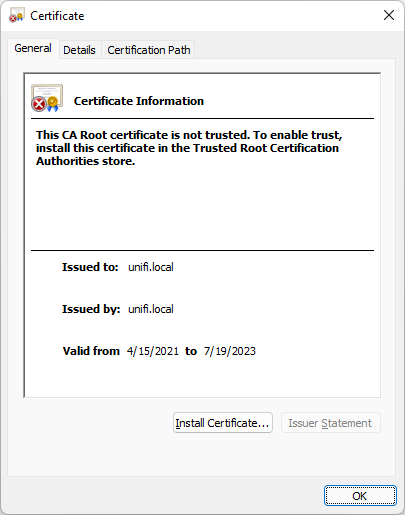
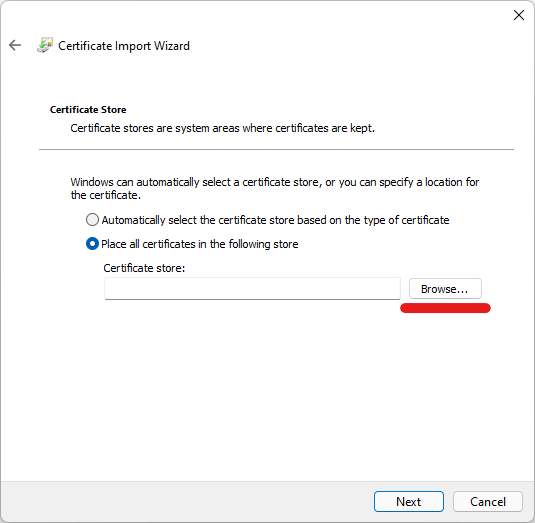
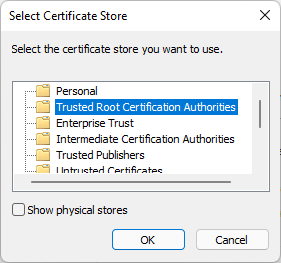
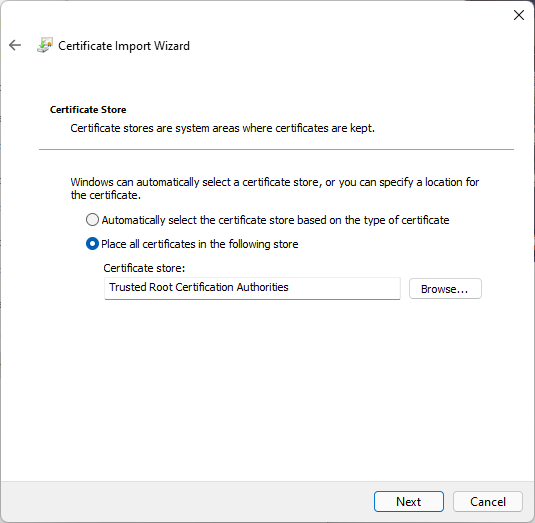
Note that it says to install the cert in the “Trusted Root Certification Authorities” store
Now we can move on to Configuring the hosts file.
Add unifi.local to system hosts file
We need to add an entry for unifi.local as the cert if for unifi.local hostname and not the controllers IP address.
We’ll essentially be following the same steps outlined in the following post.
- Launch notepad as administrator
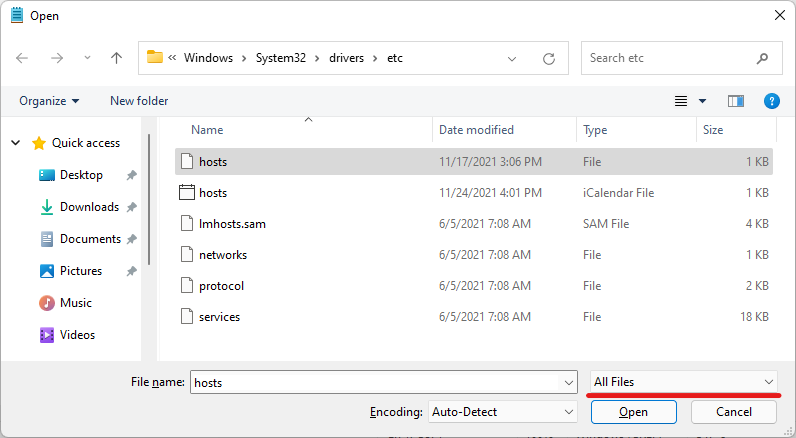
- Open the hosts file in
C:\Windows\System32\drivers\etc\
- Add the following line to the bottom of your hosts file. Change the IP address to the IP of your controller.
192.168.1.20 unifi.local
- Save the file.
You should now be set. Open a browser and got to https://unifi.local to access the UniFi Protect Controller.