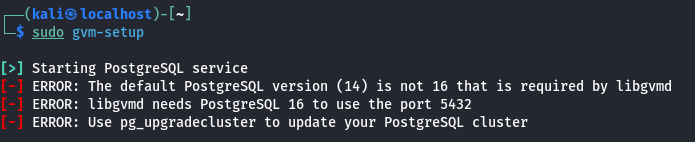
You can make the USB drive by downloading the image off of nixos.org and then use Etcher, dd, or your favorite iso to USB drive utility.
The minimum version of NixOS does not come with a GUI installer.
https://nixos.org/manual/nixos/stable/#ch-installation
The manual contains all the info needed. For a minimum install, there are a couple of steps that you need to perform, before you can install.
- Format hard disk
- Create config file
- Install
Format Hard Disk
We’ll assume that /dev/sda is our target disk. This will overwrite the disk. Make sure you don’t need anything on it.
parted /dev/sda -- mklabel gpt parted /dev/sda -- mkpart root ext4 512MB -8GB parted /dev/sda -- mkpart swap linux-swap -8GB 100% parted /dev/sda -- mkpart ESP fat32 1MB 512MB parted /dev/sda -- set 3 esp on
Format the partitions
mkfs.ext4 -L nixos /dev/sda1 mkswap -L swap /dev/sda2 mkfs.fat -F 32 -n boot /dev/sda3 mount /dev/disk/by-label/nixos /mnt mkdir -p /mnt/boot mount /dev/disk/by-label/boot /mnt/boot swapon /dev/sda2
Create a basic config file
nixos-generate-config --root /mnt
You can edit the config to make any changes you need. You may want to uncomment the user lines to setup a new user.
nano /mnt/etc/nixos/configuration.nix
Install NixOS
nixos-install
Last step is to setup the root and user password.
passwd
Reboot the machine once the password is set.
After you log in, set the user password.
passwd username